Cara Hack Wireless Dengan Wireshark Tutorials
Capture WiFi network traffic using Wireshark with any wireless network card on Windows. Video tutorial Acrylic WiFi NDIS driver with Wireshark on Windows.
Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds. If you keep your wireless router at the defaults, then hackers can control your firewalls, what ports are forwarded, and more. But never mind the hackers, what about your kids?
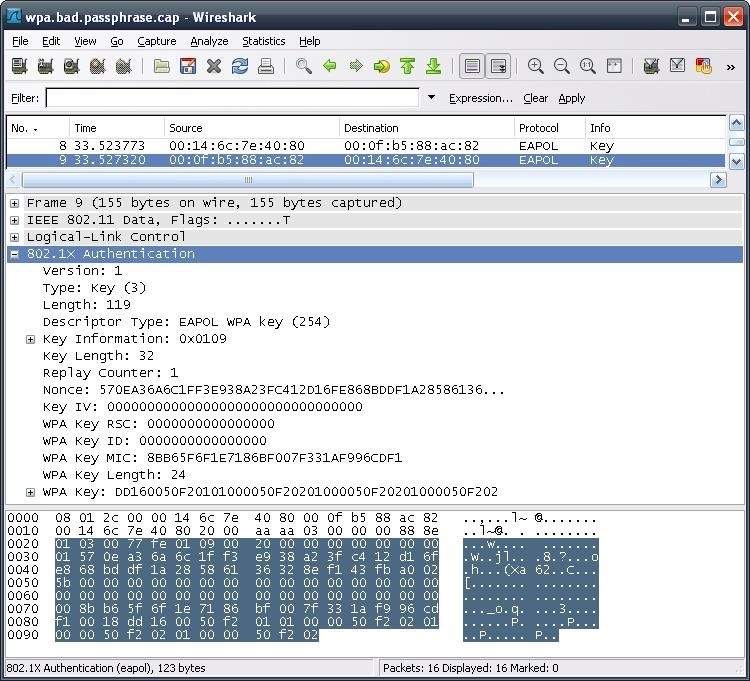
In this, we're going to take a hack at our own wireless routers to see just how secure they really are. We'll be using and, a tool.
Windows users, you can follow along if you use. Step 1 Download & Install Hydra First we need to go to the Hydra website, download Hyrda, and get everything configured. In this article, a 'cmd' refers to a command that has to be entered into a terminal emulator.
• Download Hydra from. • Extract Hydra in a nice location. Cmd: tar zxvf hydra-7.1-src.tar.gz • Change to the newly made directory.
Cmd: cd • cmd:./configure • cmd: make • cmd: sudo make install Step 2 Use Hydra on Your Router Now we're going to attack our routers. The default IP/URL to reach it at will be 192.168.1.1, so test that address in a browser to confirm it.
Shablon sertifikata ob okonchanii kursov. Similar words: (1.00) (1.00) (0.50) (0.50) (0.50) ce I Civil Engineer noun inzhener-stroitel' II Chemical Engineer noun inzhener-himik III Common Era noun nasha era IV Corps of Engineers noun inzhenernyi korpus suhoputnyh voisk ce; *1. Cache Enable; *2.
If you get a dialog box, you've reached your router. This is running HTTP basic authentication. Follow along to my video tutorial below to crack your routers authentication page.
Did you knew every time you fill in your username and password on a website and press ENTER, you are sending your password. Well, of course you know that.
How else you’re going to authenticate yourself to the website?? But, (yes, there’s a small BUT here). When a website allows you to authenticate using HTTP (PlainText), it is very simple to capture that traffic and later analyze that from any machine over LAN (and even Internet). That bring us to this website password hacking guide that works on any site that is using HTTP protocol for authentication. Well, to do it over Internet, you need to be able to sit on a Gateway or central HUB (BGP routers would do – if you go access and the traffic is routed via that).
But to do it from a LAN is easy and at the same time makes you wonder, how insecure HTTP really is. You could be doing to to your roommate, Work Network or even School, College, University network assuming the network allows broadcast traffic and your LAN card can be set to promiscuous mode.
So lets try this on a simple website. I will hide part of the website name (just for the fact that they are nice people and I respect their privacy.). For the sake of this guide, I will just show everything done on a single machine. As for you, try it between two VirtualBox/VMWare/Physical machines.
Note that some routers doesn’t broadcast traffic, so it might fail for those particular ones. Step 1: Start Wireshark and capture traffic In Kali Linux you can start Wireshark by going to Application > Kali Linux > Top 10 Security Tools > Wireshark In Wireshark go to Capture > Interface and tick the interface that applies to you. In my case, I am using a Wireless USB card, so I’ve selected wlan0. Ideally you could just press Start button here and Wireshark will start capturing traffic. In case you missed this, you can always capture traffic by going back to Capture > Interface > Start Step 2: Filter captured traffic for POST data At this point Wireshark is listening to all network traffic and capturing them. I opened a browser and signed in a website using my username and password. When the authentication process was complete and I was logged in, I went back and stopped the capture in Wireshark.